-
Check Point Research reveals a crypto wallet drainer on Google Play.
-
Cybercriminals increasingly use advanced techniques, necessitating heightened awareness and improved security measures within the crypto space.
-
The incident underscores the need for stricter app store verification processes and greater user education to recognize potential scams.
Check Point Research has unmasked an alarming fact about cryptocurrencies: a nameless pockets drainer masquerading as WalletConnect controlled to remain undetected on Google Play for over five months without being detected using safety checks.
This crypto wallet drainer further underlines the rising threats going through cryptocurrencies.
As decentralized finance (DeFi) keeps its fast ascent, users may be seduced by its attractive opportunities without complete greed for their inherent dangers. WalletConnect is a stark example of how an unregulated application can effortlessly slip beyond oversight measures and compromise individuals’ monetary assets.
We must recollect each new crypto hack’s immediate ramifications for victims and what this incident exhibits regarding future crypto wallet security risks, features, and consumer schooling within increasingly complicated digital ecosystems.
Aside from looking into this Google Play crypto scam, we will explore several factors regarding crypto allet security risks, a rising issue for the Web 3 Community.
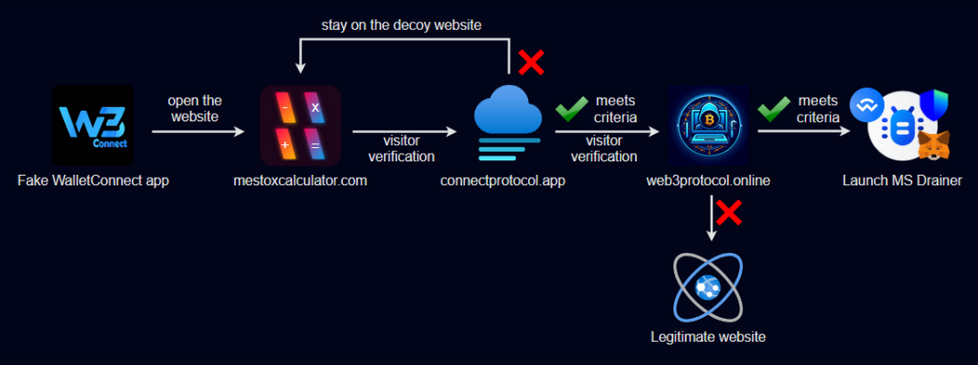
Crypto Wallet Drainer Fools Google For Months
This crypto pockets drainer operated under the call “Mestox Calculator” earlier than switching identities a couple of times so one can stay undetected.
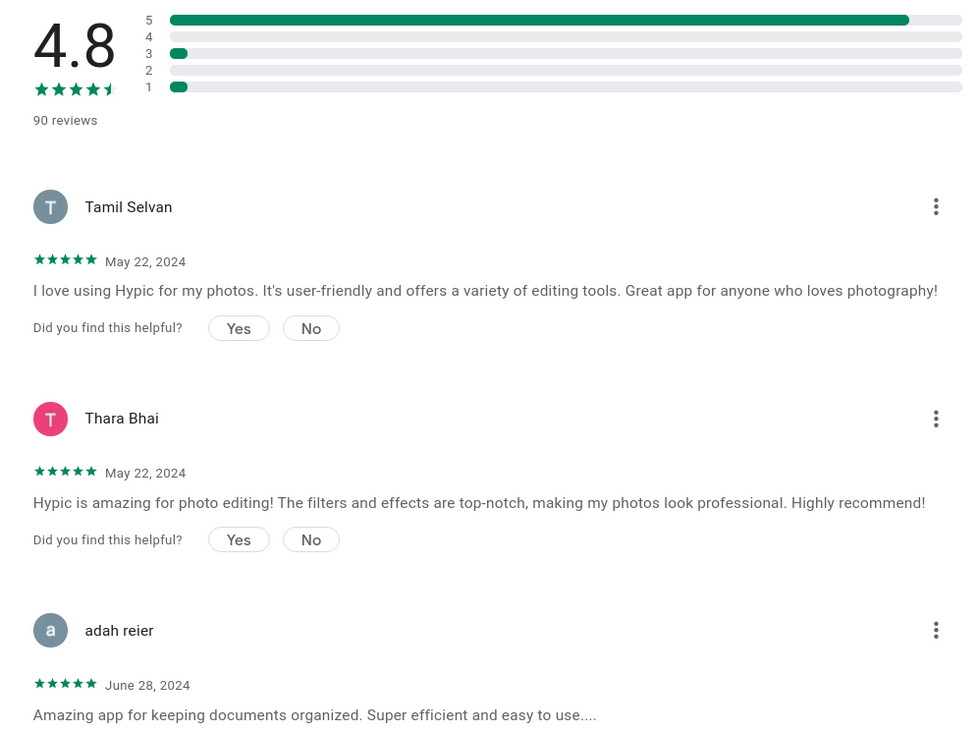
After garnering over 10,000 downloads, this crypto wallet drainer effectively exploited WalletConnect–a dependent protocol used for connecting crypto wallets with decentralized programs–via employing faux opinions and steady branding that enabled it to rank incredibly in seek effects, fooling capacity victims into wondering they had been using an authentic provider.
Google Play Crypto Scam is a clear reminder that even trustworthy platforms may fall prey to cybercriminals.
Also, Read Gora’s Breakthrough with Google: Enhancing Blockchain Oracles and Smart Contract Reliability.
Mechanism of Operation
However, the crypto hack continues masquerading as a functioning application to deepen its grip on the user’s account. The crypto wallet drainer diverts users to a malicious website, luring unexpected victims.
MS Drainer malware hired state-of-the-art hacking techniques like clever contracts and deep links in preference to conventional hacking techniques such as keylogging to maximize income by prioritizing higher-price tokens for withdrawal first, prioritizing those with greater returns earlier than targeting smaller belongings.
Unfortunately, from a financial perspective, the Google Crypto Scam has caused the organization about $ 70,000 stolen from 150 compromised crypto wallets. With the crypto bull run introducing millions to the crypto space, it’s the perfect opportunity for this kind of crypto hack.
Implications for Users and Industry
The Google Crypto Scam incident underscored the need for better equipment to battle such crypto wallet security risks. As technology continues advancing at breakneck speed, so too do the tactics employed by cybercriminals seeking easy targets among everyday consumers and seasoned investors alike.
Users must be educated about application legitimacy and remain cautious when downloading apps—even those that appear familiar or trustworthy.
Despite crypto wallet security issues growing, it’s paramount that every individual take the necessary steps to secure wallets. The WalletConnect scam is among many reminders that Web 3 and crypto still have some ways before becoming mainstream.
Recommendations for Enhanced Security
To mitigate future attacks just like the latest ones, take these sensible steps:
1. Be Wary When Downloading Apps
Always be aware of what kind of applications you intend to use. Crypto trading has become a steady income source for many individuals but also serves as a pool of resources for crypto hackers.
2. Monitor Wallet Activity Regularly
Users should robotically monitor crypto transactions to perceive any unanticipated pastime that might indicate hacks; early detection can drastically mitigate ability losses.
3. Stricter App Store Verification
Google Play and comparable systems must quickly decorate their verification procedures to hit upon fraudulent apps earlier than they attain customers, using AI-powered detection techniques or undertaking thorough guide opinions mainly centred on financial packages.
4. Promote User Education
Initiatives designed to teach users about crypto wallet security risks can arm them with the necessary knowledge to understand scams and implement protective measures.
The crypto industry is an ever-evolving franchise. Today, we have several branches, such as digital assets, NFT, DeFi, and fintech. To better understand these, one must have due diligence to safeguard their crypto wallets.
Also, Read: From Local to Global: Google’s AI Academy Aims to Position Pakistan as an AI Hub.
By adopting these techniques, people and platforms can collaborate to foster safer cryptocurrency surroundings.
Conclusion
The WalletConnect Scam is a stark reminder that as the crypto bull run continues to make millionaires, the likelihood of crypto wallet security issues increases.
The crypto wallet drainer reminds us that regulation, security, and awareness are still the main hindrances to the community. Thus, consumers, stakeholders, traders, and innovators need to prioritize security to prevent a similar crypto hack from occurring.
Each participant in a surroundings bears the obligation to safeguard themselves and maintain the surroundings’ integrity. Collaboration is important in developing robust protection protocols and upholding acceptance as true at every turn.
Let’s pledge our willpower to cultivate a subculture of vigilance and advocacy to safeguard as part of our digital destiny!
