- Bitcoin is built on the notion that crypto miners validate data or transactions through the Proof of Work
- The 51% attack is a blockchain security threat in which a group or an individual gains control of more than 50% of the computing power Proof of Work requires
- Ethereum Classic (ETC), which forked from the original Ethereum blockchain after the infamous DAO hack of 2016, has gone through the 51% blockchain attack several times.
Blockchain technology is an innovative application of a simple but efficient network that allows users to maintain data integrity safely. Throughout the years, crypto security has incorporated various blockchain mechanisms. Unfortunately, the digital world is a never-ending struggle involving blockchain security threats and blockchain security vulnerabilities.
There have been numerous blockchain threats which have resulted in the loss of millions. We are about to explain a straightforward but sophisticated attack, a 51% blockchain attack. This direct approach has crippled various crypto coins.
This in-depth analysis seeks to educate and familiarise individuals with the various threats hindering cryptocurrency’s progress.
Also, Read: Crypto security practices that will address the plague of human error in crypto
Understanding Proof-of-Work
Before diving into the 51% attack, we must understand its target functions. This creates a clear picture of the flaws and how the blockchain threat can exploit its target.
Proof of Work is the original consensus mechanism that was the building block of Bitcoin, the first cryptocurrency. PoW is a blockchain technology or system that requires a substantial but feasible effort to deter malicious uses of computing such as spam emails or denial of service attacks.

Bitcoin is built on the notion that crypto miners validate data or transactions. PoW is simply an algorithm that ensures that the blocks or transactions are only valid if they require a certain amount of computational power. Hence the work in proof of work is a crucial element.
Crypto miners must compete with others by solving arbitrary mathematical puzzles to prevent anyone from “bypassing” the system. The first to successfully duplicate this mathematical puzzle wins and receives crypto as a form of payment.
Although this mechanism powered many initial crypto coins, it proved to have several demerits. The energy consumed by individual crypto traders gradually increased; the more crypto traders were on the network they used, the more power they had.
In one survey, Ethereum generated enough electricity to power an entire nation for a year. It generally wasn’t a good show, but later crypto traders emerged, and the number of crypto miners significantly reduced.
Also, Read Blockchain Africa: The dawn of a new tech age
PoW was a blockchain technology and concept that provided crypto security without additional aid. Since many crypto traders could work on an individual mathematical puzzle, they clearly defined the decentralized nature of the blockchain mechanism.
What is the 51% blockchain attack
The 51% attack is a blockchain security threat on a blockchain network in which a group or an individual gains control of more than 50% of the computing power PoW requires. This was a straightforward but ingenious plan to undermine the PoW mechanism that most security experts didn’t think was possible.
Its simple exploitation of a blockchain security vulnerability made it fearsome.
The group/individual orchestrating the 51% blockchain attack introduces a new blockchain system within the network that the crypto security mechanism would permit. Technically speaking, it is genuinely in their right since you will require valid access to 50 + 1% of the entire network to conduct such a blockchain security threat.
The main reason this blockchain security threat was unforeseen was its sheer scale. Acquiring even 20% of a blockchain network would need a massive amount of individual computational power. In addition to gaining 51%, they would need an existing blockchain network that they can insert at any time to completely take over the blockchain system.
Like any business idea, Proof-of-Work needs hashing power; hence various companies rent out their systems to crypto miners. Attackers take advantage of this making the 51% blockchain attack much more reachable.
Hackers target smaller cryptocurrencies because the enormous power required to perform 51% attacks in the smaller ones is not immeasurable.
The attack timing is also needed since the new blockchain network has to be integrated carefully and promptly not to alert crypto security. Another frightening concept of this security is that it doesn’t necessarily require 51% of the entire network.
Conducting various network scans and using blockchain testing tools can give an attacker insight into the blockchain network. If the crypto security system is deemed inefficient or of low value, even having as little as 30% can lead to the successful exploitation of the blockchain network.
How the blockchain security threat works
Understanding the proof of work that multiple crypto miners can process a single block is essential. The one with the most computational power always emerged victorious. Once complete, the blockchain network will broadcast it throughout the network to notify other miners.
Also, Read A deeper look into crypto hacks: how they work and relate
A crypto hacker can, however, reverse existing transactions by not broadcasting his completed block. This creates an offspring/ branch of the valid blockchain network. One consists of all the valid miners while the crypto hacker solely operates the other.
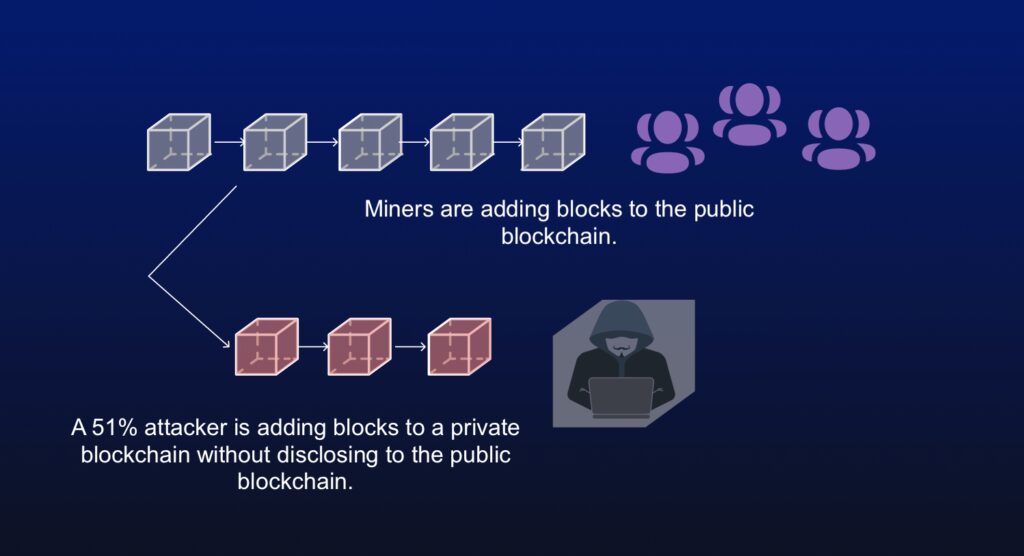
The initial balance is the same, so if they spend their coins on the existing network, the PoW mechanism won’t reflect. This creates a blockchain security vulnerability known as double-spending.
Unfortunately, the damages do not stop there, since the PoW works primarily; whoever has the most computational power shall be considered the most accurate added upon the race restarts. The hacker can now work on adding more blocks on his isolated blockchain, and he acquires more computational power than the rest.
The PoW mechanism would recognize his remote network as the “true network” and force everyone to shift to his chain. Since his isolated chain did not account for his expenditure in the original one, they can spend all over again.
The worst part about blockchain security is that acquiring 51% of the network is the main hurdle. Once a hacker achieves that mark, he can repeat the process of duplicating the chain repeatedly.
Use Cases of the 51% blockchain attack
In all manner of crypto security, it is common to expect the unexpected. Since many expected the 51% attack to target low-end crypto coins merely, they did not expect the attack on Bitcoin altcoins. Bitcoin Gold – a fork from the main Bitcoin chain – suffered a 51% attack in May 2018, leading to the theft of $18 million worth of BTG at the time.
Ethereum Classic (ETC), which forked from the original Ethereum blockchain after the infamous DAO hack of 2016, has seen 51% attacks several times.
On Sunday, 1 December 2019, 15:19:47 GMT, 603 blocks were removed from the VTC main chain and replaced by 553 attacker blocks.
Vertcoin is a Bitcoin clone that aims to be ASIC-resistant by hard forking. After conducting a thorough search using their crypto security, they identified five double-spent outputs that redirected 142 VTC coins.
Each double-spend output was a Coinbase output owned by an unknown attacker. Unfortunately, they were unable to trace them but were able to patch up the blockchain security vulnerability.
Mitigation
In reality, these attacks are genuinely brutal to perform. The miner has to have enough processing power to not only establish the isolated blockchain but also maintain it. It’s generally more accessible if the target is an upcoming cryptocurrency.
Also, Read Cryptocurrency mixer Tornado Cash creates fodder for crypto hackers
Experts noted that Proof-of-stake was possible mitigation for the 51% attack. It required the hacker to spend more money buying crypto coins than hardware. Its application was just too expensive for any crypto hacker to undertake.
With the recent migration of Ethereum to PoS, more and more crypto coins are shifting to the new eco-friendly blockchain technology. Some even consider crypto mining a legacy activity since crypto trading is far less expensive and more accessible.
Although the applications of 51% attack are simple unless you’re investing in underdog cryptocurrencies such as Monero, Solana and Tamadoge, you genuinely have nothing to fear.
The sheer power it would take to accomplish a 51% attack on Bitcoin, Ethereum and BNB is not feasible. Anyone willingly spending such a sum for a 51% attack does not need it.
Conclusion
There are multiple blockchain security vulnerabilities, and we will delve more into others. This was a mere starting point to tackle more recent blockchain security threats.
Even though 51% of attack is considered a legacy blockchain security threat, their dangers are still accurate. Investing in 51% of a network would appear as a small investment once the attacker isolates their blockchain network.
